Home >> Uncategorized >> How to write security policies
How to write security policies
Apr/Mon/2017 | Uncategorized
How to Write an Information Security Policy in 5 Minutes - YouTube

Technical Writing for IT Security Policies in Five Easy - SANS Institute

Writing Security Policies and Procedures - SecureState

How to write effective security policies - IBM

How to write an information security policy | CSO Online

How to write effective security policies - IBM

How to create a good information security policy - Computer Weekly

Technical Writing for IT Security Policies in Five Easy - SANS Institute

Writing Security Policies and Procedures - SecureState

How to write an information security policy | CSO Online

How to Develop Good Security Policies and Tips - GIAC Certifications

Writing Effective Information Security Policies - BankInfoSecurity

How to write an information security policy | CSO Online

Writing a security policy - SearchSecurity - TechTarget

Writing Effective Information Security Policies - BankInfoSecurity
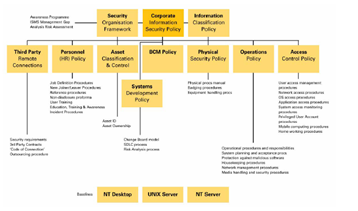
How to write effective security policies - IBM

How to Write an Information Security Policy | Computerworld

Writing Security Policies and Procedures - SecureState

How to Write an Information Security Policy | Computerworld

How to Write an Information Security Policy | Computerworld
